In S4HANA FIORI tiles are used a lot to replace traditional SAP GUI transactions.
This blog will explain how to setup the basic embedded FIORI activation and how to activate business roles for demo purposes.
Questions that will be answered in this blog are:
- How to set up embedded FIORI in S4HANA?
- How to activate business roles and its tiles?
- Where can I find more background information on the activation?
Basic activation
We will start with the basic activation. Start, via transaction STC01, task list SAP_GW_FIORI_ERP_ONE_CLNT_SETUP:
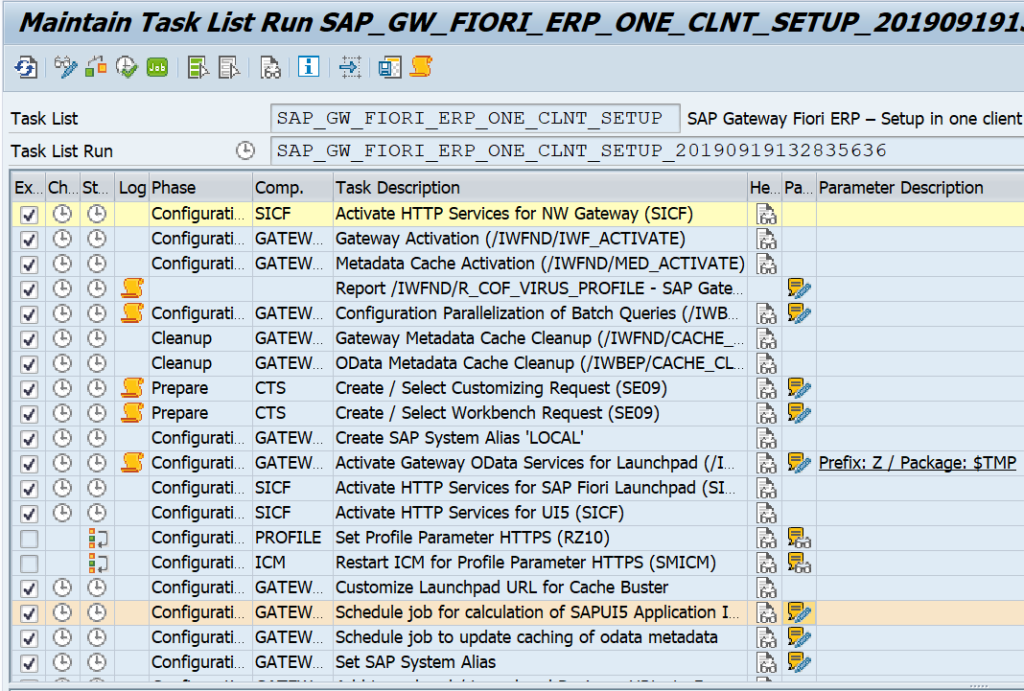
Fill all the parameters and let it run. Fix any issue that pops up.
When this is done in STC01 select task list SAP_FIORI_FOUNDATION_S4 (background note of this task list 2712785 – Fiori Setup: Initial Setup for Fiori Applications S/4):
Go into the details:
Fill out the parameters and start the task list. Be patient and let it run.
End result should be all green:
Now the basics are done. You can start to launch the embedded FIORI UI with transaction code /UI2/FLP.
If you have issues with login, please check this OSS note 2773732 - Fiori Logon page loads incorrectly in SAP_UI 752 or S/4HANA 1709.
The launchpad will be empty since you have no roles and tiles attached to your user.
Content activation of business roles
In the FIORI reference library you need to search for the role you want to activate.
Before activating roles, please make sure you have enough shared objects memory (RZ11 parameter abap/shared_objects_MB). Otherwise you wait very long to get this error:
To activate content role start transaction STC01 and select task list SAP_FIORI_CONTENT_ACTIVATION:
Task list look like below:
In the select SAP business roles for FLP content activation select the wanted business roles:
You might be tempted to select all or a lot: don't. Only select 2 to 5 maximum each time. The unpacking and activation is an intensive long running process.
Now let the task list run (be patient). If the task list run is completed, assign the generated PFCG BR roles to your user ID. Now start FIORI launchpad with /UI2/FLP and the tiles should be visible and working.
Search setup
Most FIORI apps use the S4HANA embedded search function. See this blog for setup of search.
FIORI notification setup
For setting up FIORI notifications, read this dedicated blog.
FIORI Health Check
Apply OSS note 2925879 – Fiori Setup: Heath Check. This delivers STC01 task list SAP_FIORI_HEALTH_CHECKS. Then run the task list:
Check the red logs for issues.
Background information
Not all tiles will work via this procedure. Some tiles have exceptions or additional work to do. The additional work and generic background information of S4HANA embedded content activation can be found in OSS notes:
- 2834415 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 1909, 2924004 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 1909 FPS02.
- 2947824 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 2020.
- 3085127 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 2021.
- 3236624 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 2022
- 3469488 – Composite SAP note: Rapid Activation for SAP Fiori in SAP S/4HANA 2023 FPS02
Similar notes exist for different older versions. The generic OSS note is 2902673 – Rapid Activation for SAP Fiori in SAP S/4HANA – Overview.
A good background blog on embedded FIORI content activation is this blog.
Other OSS notes:
- 2510134 – Fiori Setup: Updates for task lists for Gateway/Fiori configuration
- 2630153 – Fiori Setup: Improvements OData service activation task list
- 2739383 – Improvements for Workbench/Customizing Requests used in task lists
- 2850755 – Fiori Activation tasklist fails due to ar_srvc_launch ICF node activation failure
- 2952766 – SAP_GW_FIORI_ERP_ONE_CLNT_SETUP failing on activating OData service like: /UI2/FDM_***