In a high secure environment data access to SE16 and SM30 needs to be restricted. In many cases either IT or business still needs to maintain data via SM30 mechanism or some support people still need to see certain table data.
This blog will explain a more dedicated approach to create a dedicated transaction for each table. The generic SM30 and SE16 access can be revoked and replaced with targeted authorizations for the specific table and transaction.
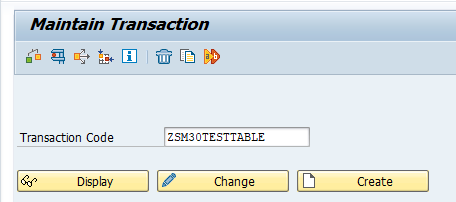
Setup transaction to call SM30 for single table
Start transaction SE93 and enter the transaction you want to created and push the Create button:
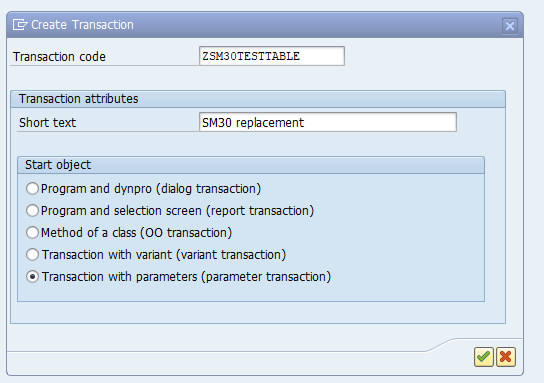
On the next screen provide a description and choose the option Transaction with Parameters:
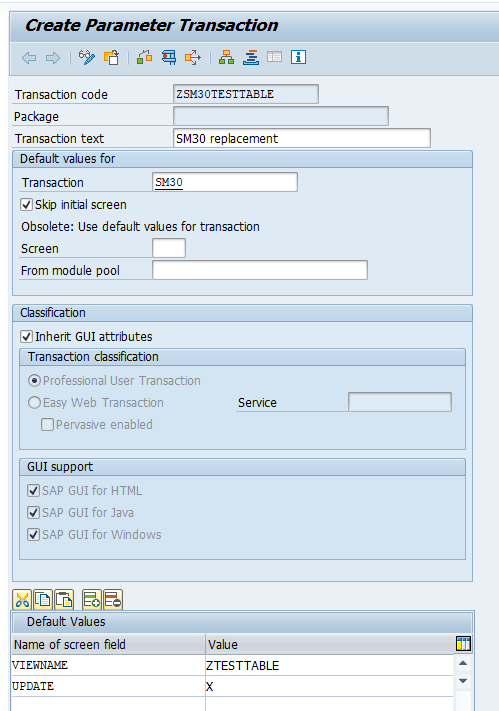
Now fill out the transaction detail:
The text is free of choice. In the transaction put SM30 (we will create a parameterized version) and select to skip initial screen. You can inherit the GUI attributes. In the default values put VIEWNAME and in the value the table you want to update. Add the second value for UPDATE with value X.
Save your work and test the transaction.
By entering the transaction code you now jump to the maintenance of the table (in our case the ZTESTTABLE as specified).
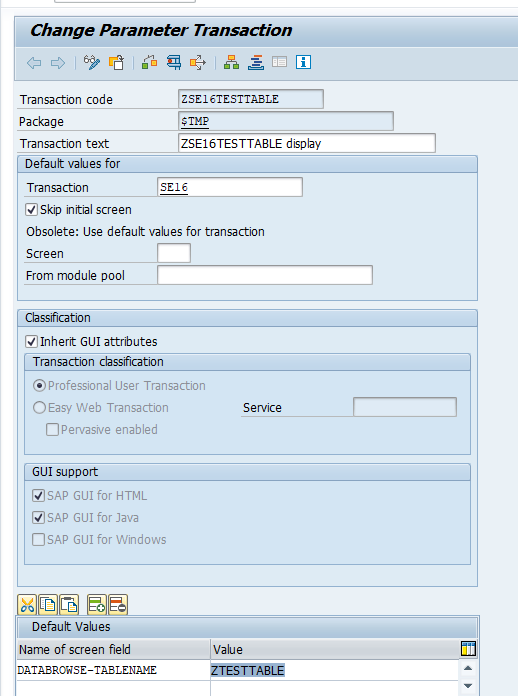
Setup transaction to call SE16 for single table
For SE16 repeat the above steps:
The text is free of choice. In the transaction put SE16 (we will create a parameterized version) and select to skip initial screen. You can inherit the GUI attributes. In the default values put DATABROWSE-TABLENAME and in the value the table you want to update.
Authorization team work
The authorization team can now remove SM30, SE16 and generic table access. Only table maintenance for this specific table is required along with access the newly created Z transaction.