In the previous blog on SAP security notes you will see that security notes popup around “Digitally signed SAP notes”.
This blog will explain more on how to implement this.
Questions that will be answered in this blog are:
- Why switch over to the new way?
- How to implement the feature to download digitally signed SAP notes?
- How to make the relevant settings?
- Where to find more information?
Why switch over to the new way?
SAP keeps improving their security in all ways. Including OSS notes. There is no direct benefit. After downloading the OSS notes, the handling is identical for old and new way.
Switching over from current way of working to digitally signed SAP notes can be done any time.
SAP has announced the following: "Post January 1, 2020, the download and upload process will stop working unless Note Assistant (SNOTE transaction) is enabled in ABAP systems to work with digitally signed SAP Notes".
How to implement digitally signed SAP notes?
There are 2 basic ways to implement (you have to do only one):
- Apply OSS notes 2508268, 2408073 and 2546220.
- Apply TCI based OSS note 2576306, which contains all the notes (and manual work) in the notes mentioned in point 1. Your system needs to be able to handle TCI based OSS notes (see this blog on how to do this).
- Follow the guided procedure
Guided enablement procedure
The guided procedure is the easiest way to apply and check the digitally signed OSS notes way of working.
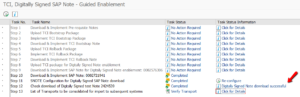
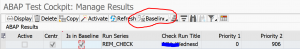
Follow the instructions from OSS note 2836302 – Automated guided steps for enabling Note Assistant for TCI and Digitally Signed SAP Notes. Attached this note is an explanatory PDF document that describes all steps in detail. After installation of the OSS note (and prerequisite notes), you can run program RCWB_TCI_DIGITSIGN_AUTOMATION, which will guide you through the steps and verifies the results at the end:
Settings after implementation
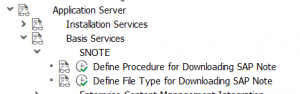
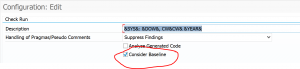
If you have done the TCI based import a new customizing node is available:
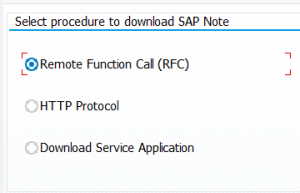
The first one (direct program in SE38 is called RCWB_SNOTE_DWNLD_PROC_CONFIG) is to set the way of downloading:
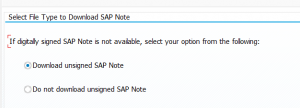
The second one (direct program in SE38 is called RCWB_UNSIGNED_NOTE_CONFIG) is to allow only digitally signed SAP notes:
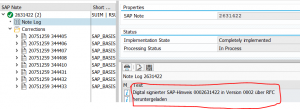
How to validate if the notes now are digitally signed?
To see if all is ok, download and implement a new OSS note. In the note log you can now see the digital signature download in the note log (in nice German words):
Known issue notes
Please read OSS note 2721941 – Download of digitally signed note – changes to configuration report and other minor changes carefully. It contains last minute fixes and changes.
Where to find more information?
More information can be found at the following sources:
- 2537133 – FAQ – Digitally Signed SAP Notes
- Presentation on handling digitally signed SAP notes
- SAP notes assistant page, section for digitally signed SAP notes
- Full implementation presentation (including changes in RFC)