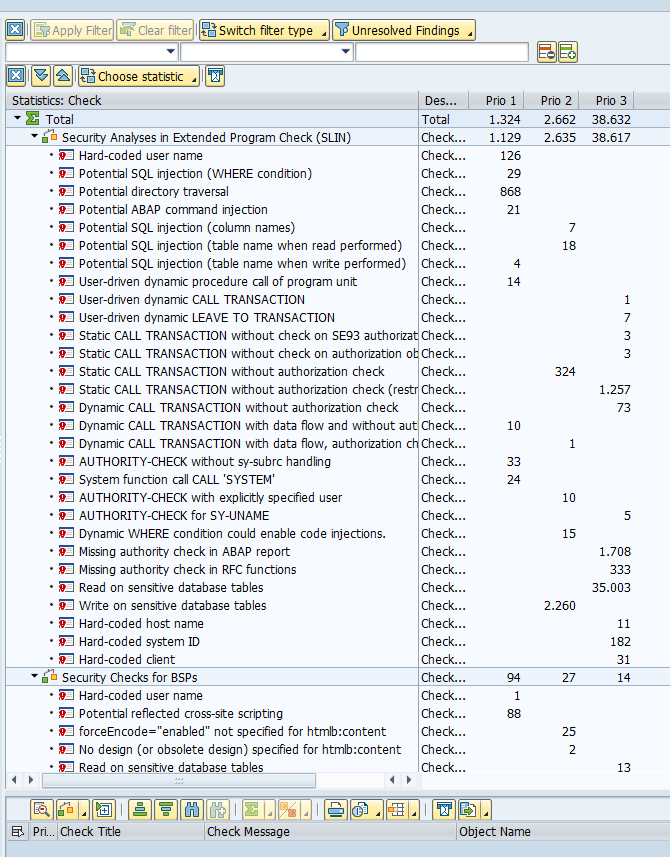
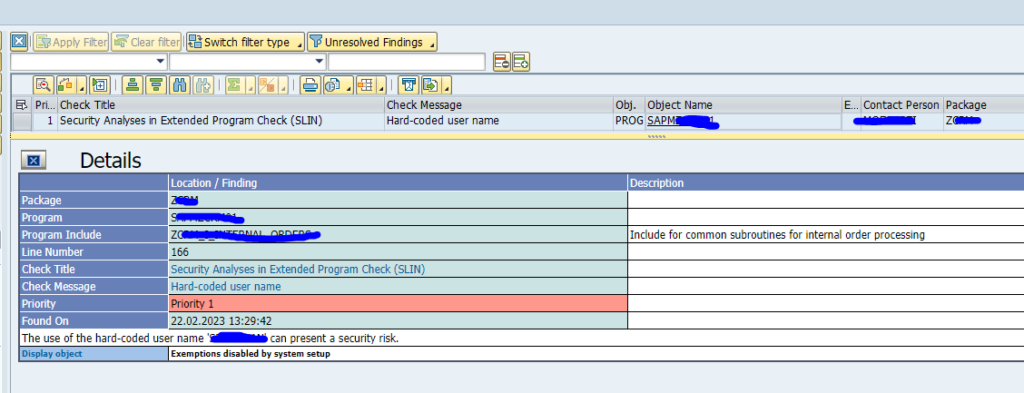
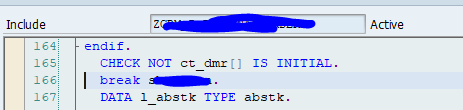
An ABAP developer can call a different transaction from a custom build program or transaction. This can be very helpful for certain user requirements and can save an end user time when the system is helping him with jumping from one transaction to the next logical transaction.
Example
For authorization this can be a bit messy.
What for example will happen with this coding:
CALL TRANSACTION 'SU01'.
Will the SU01 transaction now be called successfully or not?
SE97 TCDCOUPLES
Suppose the user does not have rights to call SU01. The coding is still trying to go to this transaction.
Depending on the value of system parameter auth/check/calltransaction a couple of things can happen:
- No check
- Always check
- Lookup if check is needed in table TCDCOUPLES
Table TCDCOUPLES links the calling transaction to the jumped to transaction and determines if the transaction authorization for the new transaction is required or not.
But what in case there is no entry or the entry in TCDCOUPLES is vague? Then it again determines on the value of parameter auth/check/calltransaction to be strict or not strict.
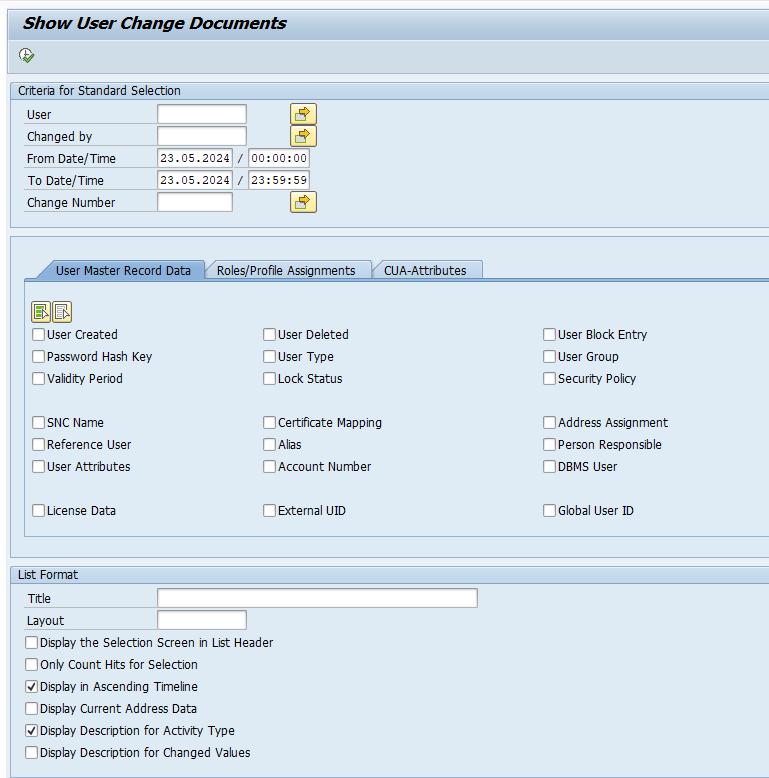
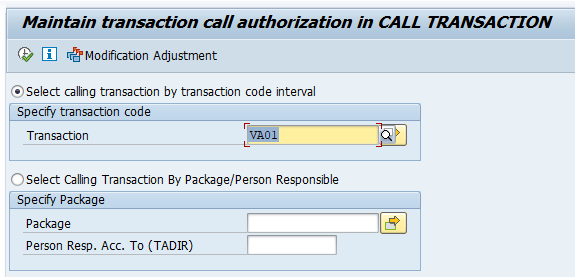
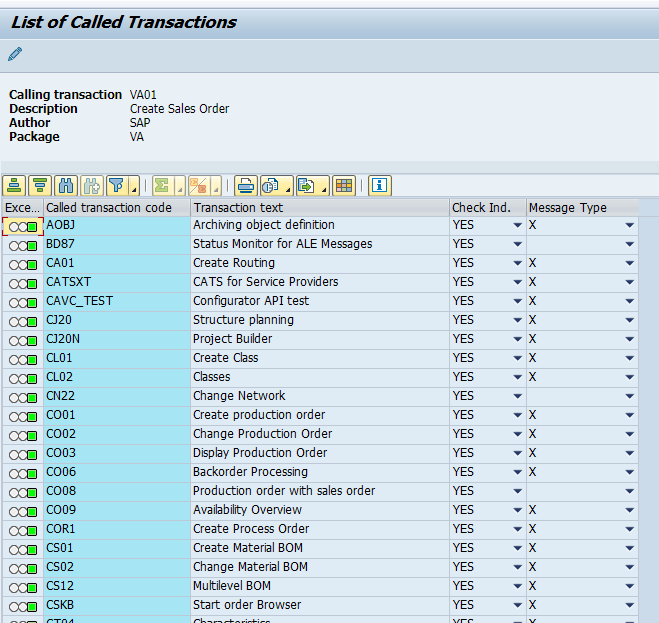
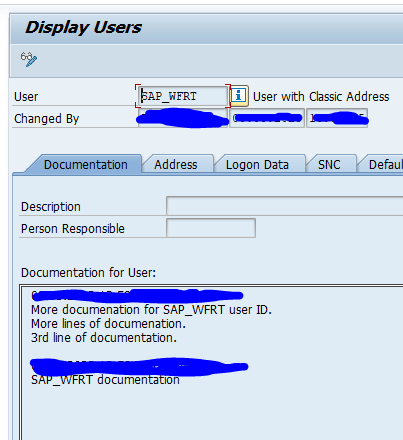
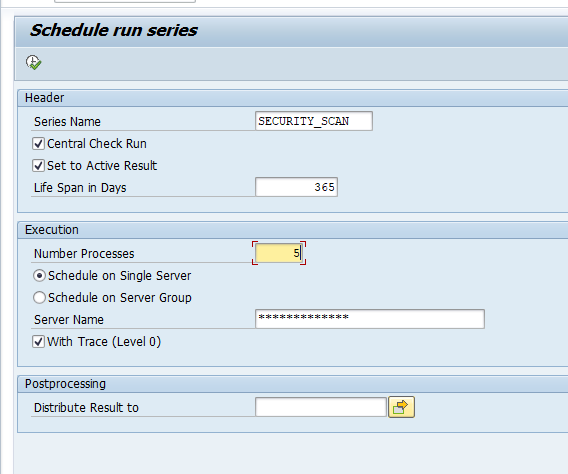
Entries in table TCDCOUPLES are maintained via transaction SE97:
Standard SAP example output:
Formal OSS note of SE97: 358122 – Description of functions of transaction SE97.
Updating TCDCOUPLES is a lot of work and no longer SAP best practice. See this SAP blog.
Correct way of coding
The correct way of coding is more simple: always indicate that the authority check is mandatory:
CALL TRANSACTION 'SU01' WITH AUTHORITY-CHECK.
In this way the coding forces the check independent of the system parameter and entries in TCDCOUPLES.
Finding incorrectly coded CALL TRANSACTIONS
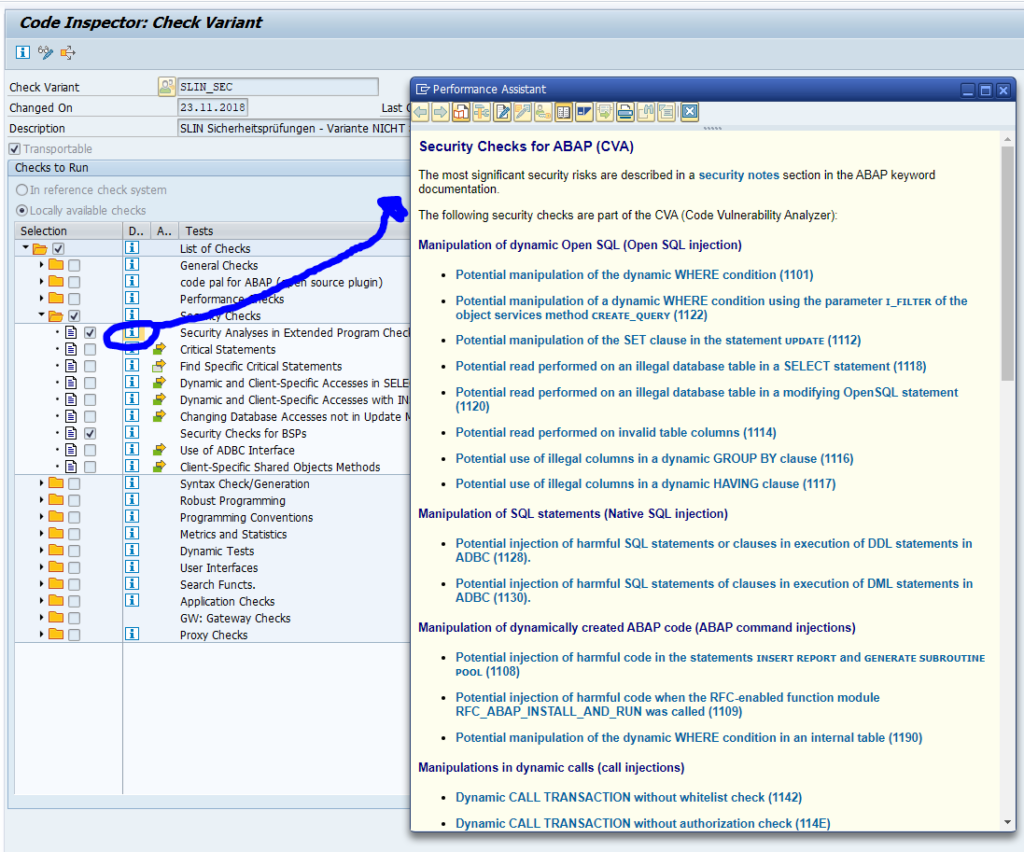
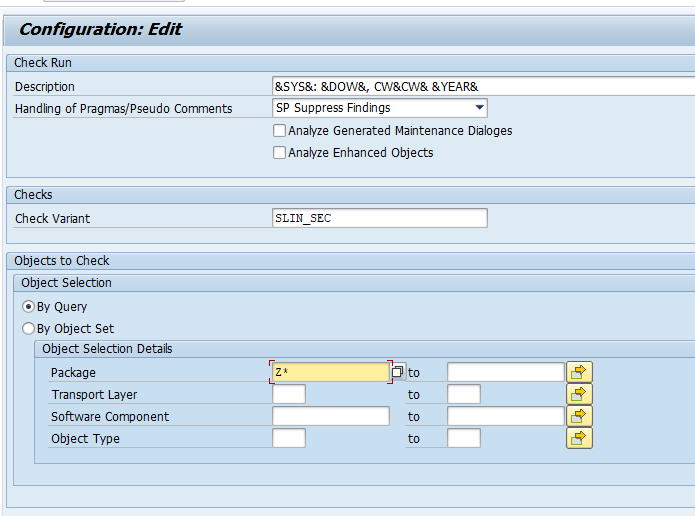
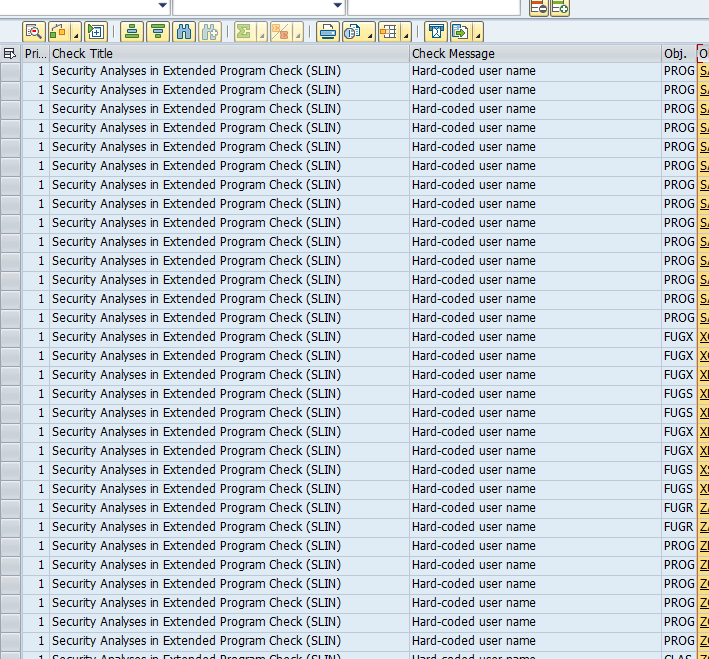
The fastest way of finding incorrectly coded call transactions is by running the SAP CVA (code vulnerability analysis) tool. This tool scans for CALL TRANSACTIONS with missing authority checks. It also scans for other variations like dynamic use of CALL TRANSCATION.
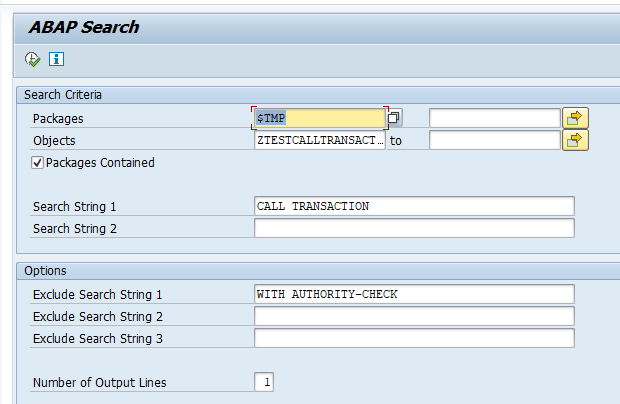
Alternatively you can use CODE_SCANNER (see blog on usage) with this special input:
Basically you tell the program to look for any program with CALL TRANSACTION and not having WITH AUTHORITY-CHECK in it. Do realize it can potentially miss programs in case there are 2 calls (1 correct and 1 incorrect). The CVA tool will not miss this case.
LEAVE TO TRANSACTION
You might wonder: what is the situation for the LEAVE TO TRANSACTION statement? That is more simple. LEAVE TO TRANSACTION will always check the user rights for object S_TCODE for the transaction.