This blog will explain the ABAP code you can use to send an email from SAP system which is in HTML format including hyperlink.
Questions that will be answered in this blog are:
- Which basis settings do I need to make for HTML mail format sending?
- What code snippets can I re-use to send a hyperlink in an email from my custom ABAP program?
Basis settings for HTML mail
In order to be able to send an mail with a hyperlink the mail must have HTML format.
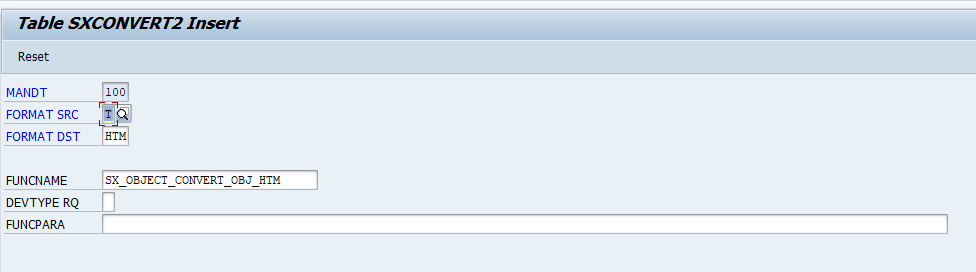
First check this table entry exists in table SXCONVERT2:
If not create it.
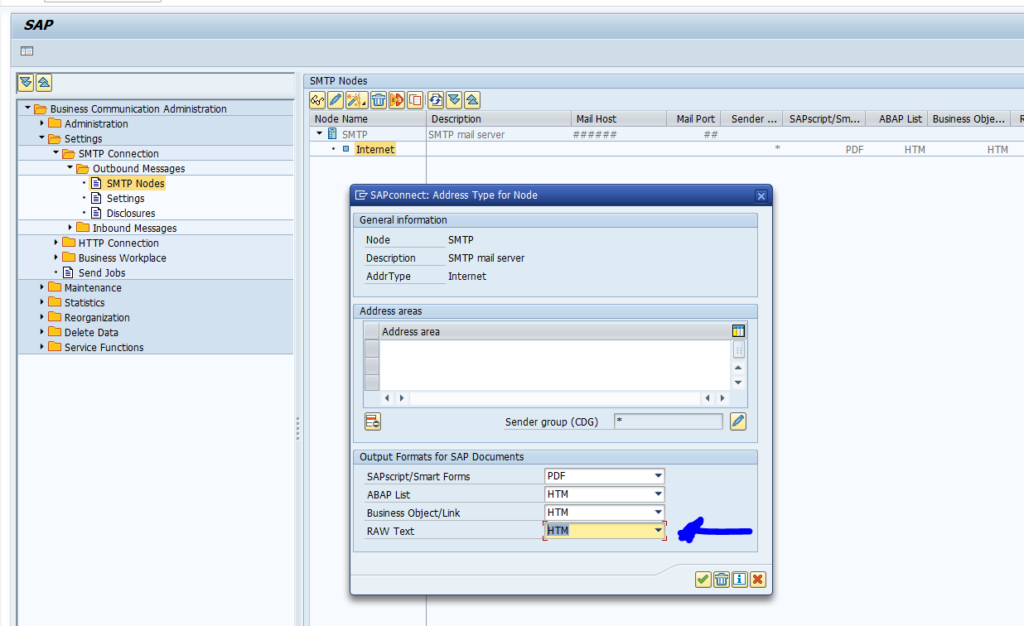
Now go to transaction SCOT and set the output format of RAW to HTM:
Save the settings.
ABAP code to mail hyperlink
The ABAP code to mail is as follows:
*&---------------------------------------------------------------------* *& Report zemail_cl_bcs *&---------------------------------------------------------------------* *& *&---------------------------------------------------------------------* REPORT zemail_cl_bcs. CONSTANTS: gc_subject TYPE so_obj_des VALUE 'ABAP Email with CL_BCS', gc_raw TYPE char03 VALUE 'HTM'. DATA: gv_mlrec TYPE so_obj_nam, gv_sent_to_all TYPE os_boolean, gv_email TYPE adr6-smtp_addr, gv_subject TYPE so_obj_des, gv_text TYPE bcsy_text, zls_text TYPE soli, xhtml_string TYPE xstring, gr_send_request TYPE REF TO cl_bcs, gr_bcs_exception TYPE REF TO cx_bcs, gr_recipient TYPE REF TO if_recipient_bcs, gr_sender TYPE REF TO cl_sapuser_bcs, t_hex TYPE solix_tab, gr_document TYPE REF TO cl_document_bcs. DATA: zlv_longstring_message TYPE string. DATA: zlt_et_soli TYPE soli_tab. DATA: zls_et_soli TYPE soli. TRY. "Create send request gr_send_request = cl_bcs=>create_persistent( ). "Email FROM... gr_sender = cl_sapuser_bcs=>create( sy-uname ). "Add sender to send request CALL METHOD gr_send_request->set_sender EXPORTING i_sender = gr_sender. "Email TO... gv_email = 'guru@saptechnicalguru.com'. gr_recipient = cl_cam_address_bcs=>create_internet_address( gv_email ). "Add recipient to send request CALL METHOD gr_send_request->add_recipient EXPORTING i_recipient = gr_recipient i_express = 'X'. CONCATENATE '<html><strong>Decission needed</strong><br/><br/>' '<tr><th style="color:blue;">Approval item</th>' '<a href=https://server:port/sap/bc/ui2/flp#WorkflowTask-displayInbox?allItems' '=true&/detail/XXX999_PGW/000000226597/TaskCollection(SAP__Origin='XXX999_PGW',InstanceID='000000226597')> click here to decide 000000226597</a>' INTO zlv_longstring_message. CONCATENATE zlv_longstring_message '</html>' INTO zlv_longstring_message. CALL FUNCTION 'SCMS_STRING_TO_XSTRING' EXPORTING text = zlv_longstring_message IMPORTING buffer = xhtml_string EXCEPTIONS failed = 1 OTHERS = 2. CALL FUNCTION 'SCMS_XSTRING_TO_BINARY' EXPORTING buffer = xhtml_string TABLES binary_tab = t_hex. gr_document = cl_document_bcs=>create_document( i_type = gc_raw i_hex = t_hex i_length = '1200' i_subject = gc_subject ). "Add document to send request CALL METHOD gr_send_request->set_document( gr_document ). * set send immediately flag gr_send_request->set_send_immediately( 'X' ). "Send email CALL METHOD gr_send_request->send( EXPORTING i_with_error_screen = 'X' RECEIVING result = gv_sent_to_all ). IF gv_sent_to_all = 'X'. WRITE 'Email sent!'. ENDIF. "Commit to send email COMMIT WORK. "Exception handling CATCH cx_bcs INTO gr_bcs_exception. WRITE: 'Error!', 'Error type:', gr_bcs_exception->error_type. ENDTRY.
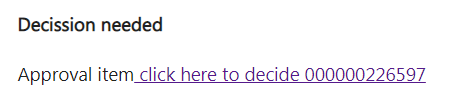
The end result is as follows in the mail:
The hyperlink in the mail jumps to the URL, which in this case is the URL link to this specific workflow item in the FIORI inbox.
The coding explained
We use the CL_BCS class from SAP. BCS stands for Business Communication Service. This class provides all modern options to send mail. We set the sender and receiver.
We now build the mail in HTML. All is stored in zlv_longstring_message. We start with the <html> tag, and a header text in bold (strong). Then we add the text with the hyperlink (a href) in blue color.
The hyperlink towards the FIORi inbox contains ‘ characters. This does not convert well for all further on steps. So we replace ‘ instead the ' text. This ' text is the HTML character coding for an apostrophe (‘). In this way there is no misinterpretation at any browser.
At the end, we add the closing tag </html>. Now the HTML build up is ready and can be used to send.
The HTLM is converted via function modules SCMS_STRING_TO_XSTRING and SCMS_XSTRING_TO_BINARY to a binary. This binary is set as document with type HTM to the mail. The mail is then sent with immediate flag.