Despite the fact that this is a know issue, in many cases still it is seen that the SAP web administration interface is still set to fully public. This way an attacker can still retrieve vital release information.
You should check this carefully, also for newer system installations, this might be not ok.
Questions that will be answered in this blog are:
- What is the web administration interface?
- Why is it dangerous to have this public?
- How to close the gap and make the web administration interface shielded again?
What is the web administration interface?
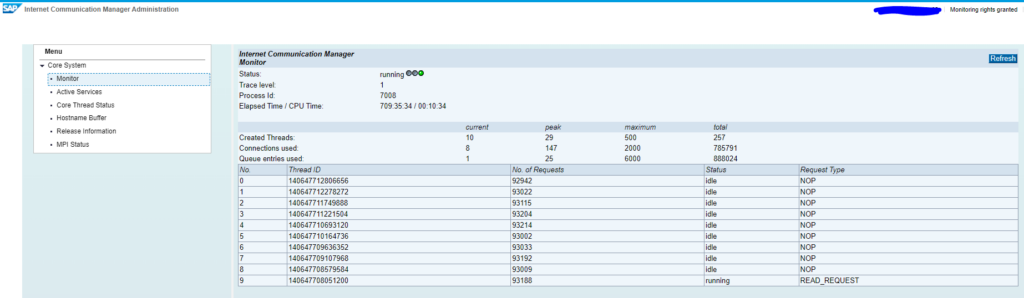
The web administration interface can be started on your netweaver system by using a browser and keying in <host:port>/sap/admin/public/index.html:
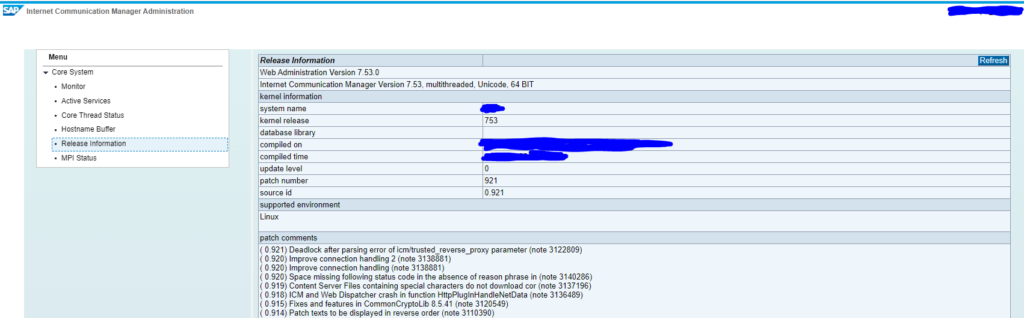
Here you can see the status and also the version information:
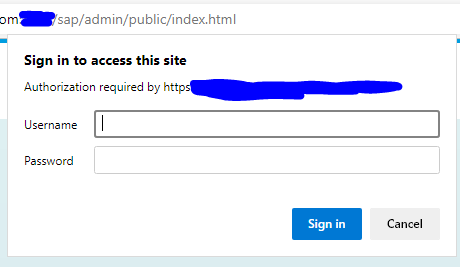
If you keyed in the URL and you got a password prompt like this:
If you did not get it, that means this page is still public.
Why is this public release information dangerous?
This page is present in ABAP, JAVA stacks and webdispatcher. Portals and Netweaver gateway systems are often exposed to external world for partners, customers and suppliers. If you did not do a good job on security with reverse proxies and the SAP systems themselves, this page is available on internet. Hackers scan for it, get the release information and know if you are vulnerable or not.
Dangerous? Yes, very. See the last very high Hotnews security note on ICMAD:
- 3148968 – FAQ for SAP Security Note 3123396 [CVE-2022-22536] Request smuggling and request concatenation
- 3123396 – [CVE-2022-22536] Request smuggling and request concatenation in SAP NetWeaver, SAP Content Server and SAP Web Dispatcher
How to solve the issue?
The solution is described in OSS note 2260323 – Internet Communication Manager (ICM) 7.20 security settings and more specifically in OSS note 2258786 – Potential information disclosure relating to SAP Web Administration Interface.
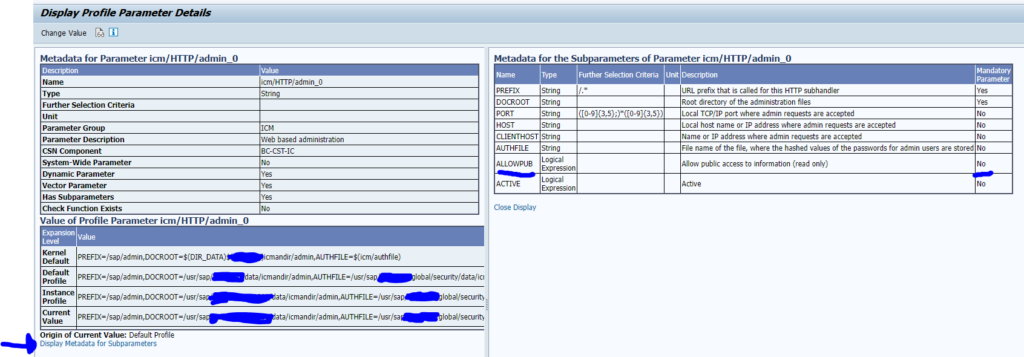
The solution is to set the sub parameter ALLOWPUB (it is a sub parameter of icm/HTTP/admin) to NO. See screen shot on how to see the sub parameters:
Checking if it is done properly is simple: start the page again and see that it disabled: