This blog will explain one of the most useful new tools from SAP when having to find bugs in standard SAP coding. The ANST (automated notes search tool) is not receiving the recognition that is should get. In usability it is same ease as the SNOTE tool.
If you love SNOTE you will also love the ANST tool! Just try it out.
Questions that will be answered in this blog:
- What is the ANST automated notes search tool?
- How does is work?
- Why should I always use this tool before submitting an incident to SAP?
ANST (advanced notes search tool)
The ANST tool can help you in:
- Quickly finding OSS notes for your issue
- Check if you Z code is causing the issue or dump, or it is a standard SAP issue
OSS note 1818192 is the ANST FAQ note which also has the minimum version. This note also has an extensive explanation. The how to use below is just a summary.
OSS note 2605555 also contains an excellent PDF inside as attachment, that gives a step by step manual.
How to use the ANST tool?
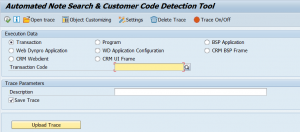
Start transaction code ANST.
If you launch it for first time you might get an error "ANST001 Fatal Error. Customizing table is not filled". If this is the case follow the solution steps in OSS note 1909768.
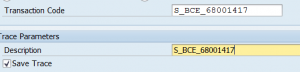
In the transaction code box key in the transaction where you have the issue. As example we will use transaction code S_BCE_68001417 (search for authorizations by complex criteria). The user admin is complaining about an incorrect number of selected authorizations that are shown in that transaction.
So key in the transaction code and description (you can keep it same).
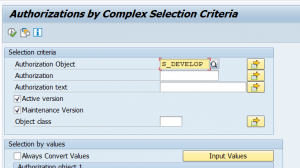
Now press execute: the transaction will be called. In the authorization object screen fill out S_DEVELOP and execute again to get the results:
Now leave the transaction recording.
In the left bottom of the screen you can see the recording being written into the trace file:
Depending on the complexity and amount of screens you have passed this can take up to 1 to 10 minutes.
The result is shown after the trace file. The result is sorted per SAP module. If you open the details, you can also see the exact program blocks that were hit during the recording.
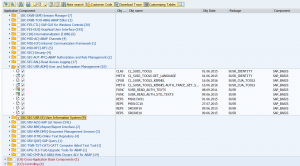
Now you can select the modules (if wanted specific code blocks) where you thinks is the issue. After selection hit the Note Search button. The SAP system will now connect to SAP service marketplace and look for the most recent notes for your version, which have not yet been implemented.
The middle note seems to be very relevant. From this screen you can can already link to the note (click on note number) and start download to SNOTE already.
Tips on the selection of the components: 1. Never select more than 1000 components: ANST will reject this 2. The less components you select the faster you get results, and shorter list of potential notes as well 3. If you want you can later retrieve the recording and make a different search on different components: no need to re-record 4. Most of the times you can ignore the basis and cross application and basis notes 5. Run the recording and the result together with your functional consultant: he can help filter the components and select useful notes
Changing settings for maximum amount of notes
Especially in the basis or core ABAP area you will notice that ANST cannot read more than 1000 notes at once. This is a default setting you can easily change. In the main ANST screen hit the Settings button and scroll to the right to increase the maximum notes number:
Using ANST to analyze short dumps
The ANST tool can be used as well to analyze short dumps. Just start the ANST tool and run the steps including the step where the dump occurs. After the dump the ANST tool will trace the modules including the point where the dump occurs.
Make sure OSS note 2535278 is applied: this contains bug fix for the short dump case.
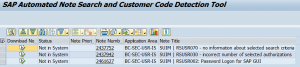
Checking for customer code issues
After the trace file is generated and you have searched for OSS notes, it can be there is still an issue caused by your own customer code. To exclude this (or to check it anyhow), you have to use the button Customer Code from the trace result screen with all the components. Be a bit patient while the tool is scanning for modifications, user-exits, BADI implementations and enhancement spots it came across in the recording.
If you want to analyze implicit and explicit enhancements as well with ANST you must apply OSS note 2408785 first.
ANST clickable demo
SAP has made a nice clickable demo to show you how it works: link to demo.
Use of ANST tool before submitting incident to SAP
Even if the ANST tool does not help you search for the correct OSS note for your issue, the ANST tool can help you in speed up of the incident solution for SAP.
If you want to report the issue to SAP as an incident download the ANST trace file. If you report the incident mention:
- ANST tool is used and add the recording
- Add list of already implemented OSS notes
- You already checked for customer code
With this information the first line processor will have a quick job assigning the incident to the real issue solvers in Walldorf. This will save you valuable time, since the first line normally come with simple list of notes, or also run the ANST tool themselves, and then come with obvious notes.
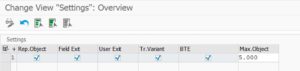
Increasing the maximum number of objects limit
If you are using the ANST tool on a transaction with many objects (for example ME21n purchase order), you will notice that you cannot search for more than 1000 objects at the same time. Then you have to open subsection and select subtree and run it more than once with different selections. But sometimes one node really expands into more than 1000 objects. In this case, you best increase the maximum object limit. In ANST start screen choose the Settings button can increase the Max.Object counter on the far right of the settings (scrolling required)
Needless to say, more objects do take more time to analyze. But it is worth the wait.
Relevant OSS notes
Some interesting OSS notes to review:
- 2383525 – ANST – How to use ‘Trace On/Off’ option
- 2735032 – ANST: Scan Source Code for Implicit Enhancements
- 3127184 – How to deactivate ANST
- 3205109 – ANST: Adding Document Type to input file parcel box scenario
When analyzing very large transactions, you might face CX_SY_CONVERSION_OVERFLOW dump. For workaround read this OSS note: 2921867 – ANST: Dump “CONVT_OVERFLOW” “CX_SY_CONVERSION_OVERFLOW”.
Other errors and bug fix notes:
- 3102008 – ANST error Web trace cancelled by the user Message No. ANST004
- 3200710 – Text symbol 008 is an original text and cannot be deleted or renamed
- 3167427 – ANST: Improvements to Note Search Output Result
- 3321871 – ANST: To fix CONVT_OVERFLOW error while performing trace
While switching to new SAP support backbone you might get a connection error. Follow the instructions from OSS note 2781045 – ANST / ST22 note search “Connection cannot be established” to solve it. Also apply OSS notes 2730525 – Consuming the Note Search Webservice and 2818143 – SEARCH_NOTES- Implementing SOAP Based Note Search.
And: 2829951 – Error while calling ANST Note Search WebService.
ANST for web applications and FIORI
ANST can also be used for web applications and FIORI. See this blog.