This blog series will explain the process of hacking SAP password hashes: also know as SAP password hacking. The process of hacking will be explained and appropriate countermeasures will be explained.
In this fifth blog we will focus on optimizing the speed of attack. The preventive measures will focus on reducing the attack speed.
For the first blog on attacking the SAP BCODE hash click here.
For the second blog on attacking the SAP PASSCODE has click here.
For the third blog on attacking the SAP PWDSALTEDHASH has click here.
For the fourth blog on advanced topics, like the rule based attack, click here.
For more on extended word lists, click here.
Questions that will be answered in this blog are:
- How to optimize the attack speed?
- How to optimize getting hashes converted into real passwords?
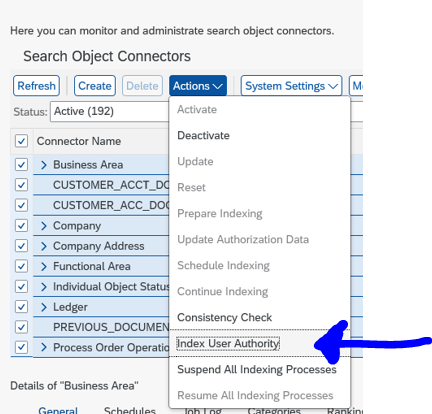
Optimizing the attack
First check if you can get hold of PASSCODE or preferably BCODE hashes. These ones are 10 to 20 times faster to hack than PWDSALTEDHASH codes.
Assuming the administrators have done their work and only PWDSALTEDHASH remains, there are still options to speed up the attack.
Get faster graphical card(s)
Don’t do password hacking on a laptop. The graphical card in any laptop is simply too slow. Use a gaming specification graphical card or cards (cost range is about 300 to 500 dollar or Euro per card).
Preparation of the attack
First thing to do is to get the password rules. Most common is 1 letter, 1 digit, 1 special and minimum length of 8. But differences occur. If for example minimum length is 10, you can adjust your dictionaries to remove all small words that will not comply.
Check the language: use the webster dictionary for English in all cases, but based on language of the company, you must use German, French, Spanish, Italian, Dutch, etc dictionaries as well.
If possible filter out high potential targets from you list. It is best to have a high value administrator or CEO, then a warehouse person who can do simple movements and write time.
Sequence of attacks
Start first with your library of most frequently used passwords. Maybe there is already a hit.
You will be surprised that about 1% will hit.
Second run is with a list of company, product and department names. If you want to target company called TARGET with product name PRODUCT, make a special file with names like:
Target2021!
Product2021!
Use the password rulebooks to generate as many variations as possible (examples are T@rget2021, Pr0duct2021!).
You will be surprised that about another 1% will hit. Who is using these simple to guess passwords? More people than you think!
Third run should be dictionary run with rulebook. Start with English and primary language of the company. Most successful Rule is word plus digit plus special.
You will be surprised that about another 1 to 3% will hit.
Pending on the speed and sizes the rulebook is a very good one to run for a longer time (consider 1 week constantly running this).
Fourth run should be a keyboard walk rulebook. The keyboard walk contains passwords like QWERtyui1234%^&*, or 1qaz@WSX (walk on keyboard…).
You will be surprised that about another 1% will hit.
Re-using the output file to generate new attack: fingerprint attack
When your first attacks are done, there is one final surprisingly successful last attack possible. For this you take your file with all the passwords you have already cracked.
These passwords you now cut into 2. Example Target2021! is cut into:
T and arget2021!
Ta and rget2021!
….
Target2021 and !
And the word itself Target2021!
Now you have 2 files. Use these into a combinator attack mode (see hashcat wiki for the exact syntax to use).
This procedure is called a fingerprint attack.
This might give surprising results like TargetProduct2021!
This attack will bring a surprising high number of hits. The better the first passwords you have cracked, the better the result here. Save this attack till last, since it can be a very lengthy one, and a lot of duplication with the previous attacks can happen.
Strengthening password technical strength
The ABAP password can be made more strong by technical means, by increasing the hash salt size. This will take longer time to crack. OSS notes:
- 2076925 – Additional SHA password hash algorithms supported
- 2140269 – ABAP password hash: supporting salt sizes up to 256 bits
Read more in this dedicated blog on password hash strengthening.