This blog series will explain the process of hacking SAP password hashes: also know as SAP password hacking. The process of hacking will be explained and appropriate countermeasures will be explained.
In this second blog we will continue with more complex attacks on the SAP password hashes and will also explain more preventive measures. Now we focus on the SAP PASSCODE hash.
For the first blog on attacking the SAP BCODE hash click here.
Questions that will be answered in this blog are:
- How to attack the PASSCODE from the BCODE?
- How does the hybrid mask attack mode work?
- How does the combination attack mode work?
- What more can I do to prevent a password attack?For follow up blog on hacking SAP PWDSALTEDHASH, click here.
For follow up blog on improving attack speed by applying rule-based attack, click here. And the blog on optimizing the attack. And the blog on extended word lists.
How to attack the PASSCODE from the BCODE?
In the previous blog we have seen how easy it is to get the passwords from the BCODE. The BCODE is capturing the first 8 characters of the password in capital mode. The other characters of the password are not stored in the BCODE, but in the full PASSCODE. If the password is length 8 or below, you can already logon with the found BCODE password.
Now lets assume company password policy is:
- Minimum password length is 10
- Minimum 1 digit, 1 letter upper case, 1 letter lower case, 1 special
Pretty safe you might think.
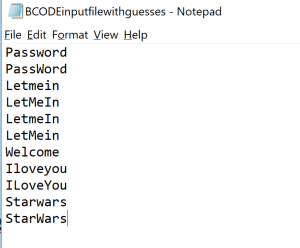
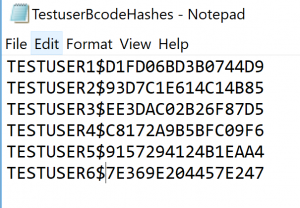
We will use the previous 5 guessed test users. Their passwords from BCODE were: PASSWORD, LETMEIN, WELCOME, ILOVEYOU, STARWARS. We don’t know exactly which letters in the passwords are uppercase and which ones are lowercase. But we can make educated guess here, which we store in notepad file:
As you can see these are logical variations. Most people use password as they type: First letter in upper case, rest in lower case.
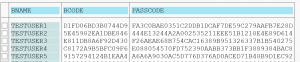
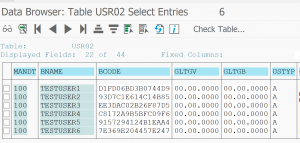
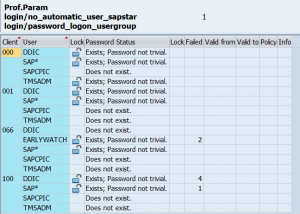
Getting the PASSCODE from USR02 table
We use one of the many methods to get the PASSCODE hash strings from the USR02 table:
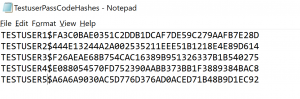
And we put this into notepad file with user name and $ for separator:
Hybrid mask attack
What we will do is use a so called hybrid mask attack. This attack uses certain patterns.
The first pattern we will use is use the file with the BCODE guesses and at the end at a digit and special character.
To start the hacking process go to the CMD command prompt and proceed to the hashcat directory. Then key in this command:
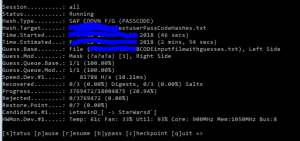
hashcat64 -a 6 -m 7800 -p : --session=all -o "C:\HC\TestuserPassCodeHashes_found.txt" --outfile-format=3 --markov-disable --remove --gpu-temp-abort=80 "C:\HC\TestuserPassCodeHashes.txt" "C:\HC\BCODEinputfilewithguesses.txt" ?d?s
Explanation of the command: 7800 means the hashes are SAP PASSCODE. Output goes to _found file. Input is the TestuserPassCodeHashes file. The text fie with the guesses is then combined with ?d?s. This means take every entry from the file and add first a digit, then a special. This will then try for example Password1!, Password2!, ….Password1@, Password2@, etc.
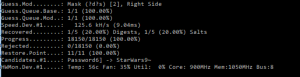
Result (after 1 min or so):
Password found: Password1! for testuser1. The output is in the output file. And the found hash is removed from the input file.
Hybrid mask patterns
Some patterns that can be used:
?l = letter, small caps
?d = digit
?s = special
?a = all possible input characters
If we continue with our example: we now will not scan for digit special combination but for any 2 or more characters. To do so: replace in the previous command the ?d?s with ?a?a.
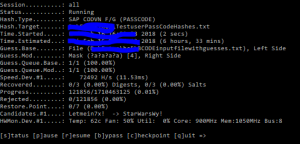
After that we can run with ?a?a?a to find any combination with 3 characters at the end. Runtime: only 4 minutes:
Only when we add ?a?a?a?a for 4 characters runtime starts to increase to 6 hours:
After these runs we have found: Welcome123! for testuser3, IloveYou@9 for testuser4 and Starwars99*& for testuser5.
Combination attack mode
The above method is fast and almost always guaranteed to work. But is will only work for short extensions. There is even a faster way, but this method does not have full guarantee.
What we will do is construct a file with popular password extensions after the main word:
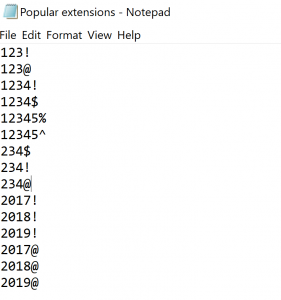 real file is much, much longer…
real file is much, much longer…
This file we will combine with the file of the already found words from the BCODE part. The combination of two files is called combination attack.
To start the hacking process go to the CMD command prompt and go to the hashcat directory. Then key in this command:
hashcat64 -a 1 -m 7800 -p : --session=all -o "C:\HC\TestuserPassCodeHashes_found.txt" --outfile-format=3 --remove --gpu-temp-abort=80 --gpu-temp-retain=70 "C:\HC\TestuserPassCodeHashes.txt" "C:\HC\BCODEinputfilewithguesses.txt" "C:\HC\Popular extensions.txt"
The attack mode 1 means combination attack to combine the two files.
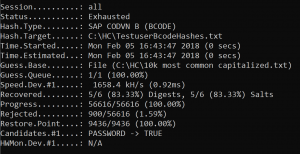
After running this mode the Testuser2 password pops up: Letmein2018).
And yes: years in passwords are pretty popular.
End result
End result after all the different attacks:
And it really didn’t take long time. One overnight session is sufficient.
The real live sequence of cracking would be to start with the popular extensions to remove the quick wins. Then time can be spent on the hybrid mask attack: this attack goes faster when there is less input.
Preventive measures
Preventive measure 1: forbid simple password parts
By filling table USR40 you can forbid simple password parts to be used. Think about filling this table with words like:
- Your company name
- password
- welcome
- letmein
- The current year
- All the full names of the months (january, etc)
- ….
For more inspiration see list of most used passwords on Wikipedia.
Preventive measure 2: forbid display access to password tables
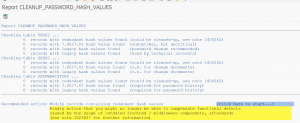
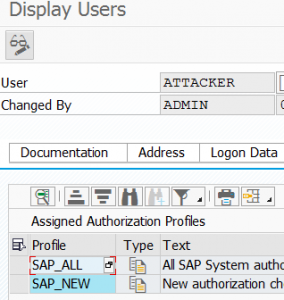
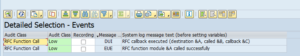
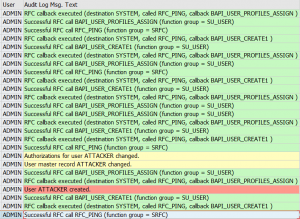
Forbid access to password tables. The hashes are stored in tables protected by the SPWD object. Don’t grant read access with S_TABU_DIS authorization object to this table group. Check via SUIM who currently has access and restrict it to only people you think really need it.
More information on the access protection can be found in OSS note 1484692.
Next blog
The next blog will explain on hacking PWDSALTEDHASH.