SAP has released S4HANA readiness check 2.0. Please read this blog on the new tool version.
If you want to use old version, please read on.
This blog explains the new tool for SAP customers to prepare for S/4 HANA upgrade: S/4 HANA readiness check.
Questions that will be answered are:
- What is the S/4 HANA readiness check?
- How to execute it?
- What results can I expect?
S/4 HANA readiness check
The S/4 HANA readiness check is a tool from SAP that can help you prepare for S/4 HANA upgrade. The tool is a web based online tool running in SAP cloud that is using 2 files with data from your system:
- Extract from your customer code
- Usage data of transactions measured in your system (based on ST03N data)
The outcome is online report with list of potential improvements in S/4 HANA that might be relevant for your business and list of potential issues when upgrading caused by custom code or by generic changes by SAP.
The end user guide of the tool can be found on the SAP site.
Execution of S/4 HANA readiness check
The main note for the readiness check is 2290622. This note describes that there 2 ways to run the check:
- Via solution manager
- Directly
The direct approach is the most easy. The exact steps are always updated in OSS note 2310438. Carefully implement all the prerequisite notes mentioned in this note.
After this is done 2 programs will be available.
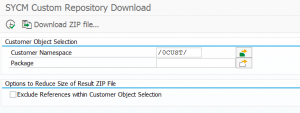
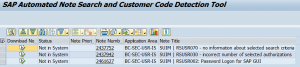
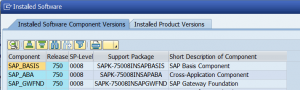
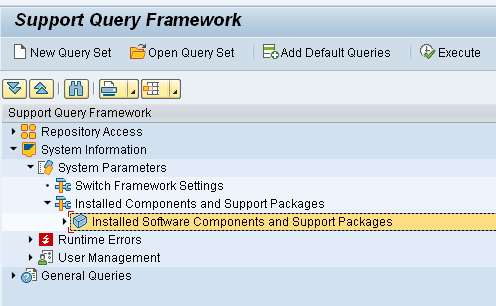
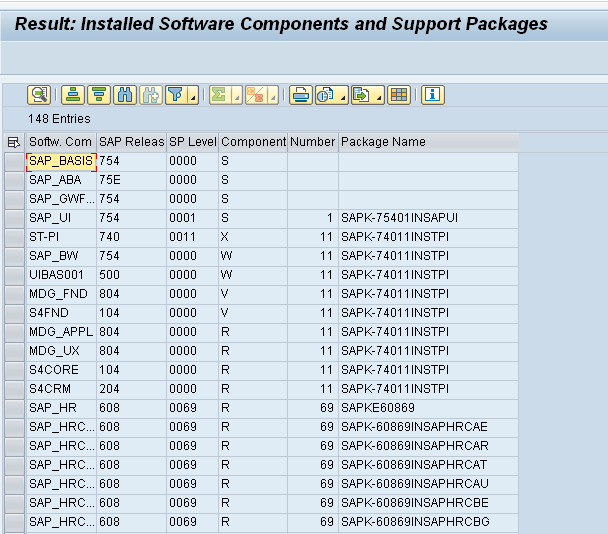
Program SYCM_DOWNLOAD_REPOSITORY_INFO will download the ABAP custom developments.
The program will check if the where-used index is up to date. If not it will refer to OSS note 2234970. This note can be bit confusing. But basically what you need to do is run program SAPRSEUB in the background (and wait up to 2 days on larger system with many custom code!!).
Please note the following: As a prerequisite for SAP Note 2185390 or the program SYCM_DOWNLOAD_REPOSITORY_INFO, please start only the program SAPRSEUB! Do not start SAPRSEUC. If you use an MSSQL database, you must implement SAP Note 1554667 before starting SAPRSEUB; otherwise, database problems occur. More on ABAP where used index via SAPRSEUB see blog link.
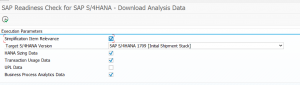
The second program will capture analysis data: TMW_RC_DOWNLOAD_ANALYSIS_DATA.
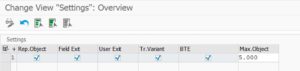
You will have to start this program a few times. Every time it will launch a new batch job for each tick box you have selected.
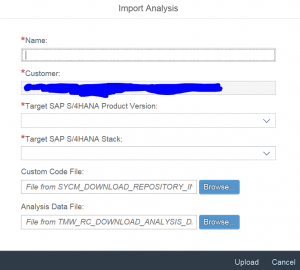
Both of the programs will deliver you a zip file that you store on local PC or laptop.
These result files you upload in the SAP cloud part of the tool on the SAP support portal: https://launchpad.support.sap.com/#readiness.
Now you have to wait until the analysis is done.
Result of the S/4 HANA readiness check tool
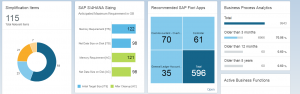
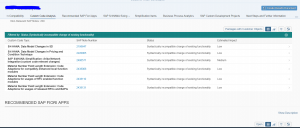
When the analysis is finished you first enter the dashboard:
When zooming in you will reach the detailed screens with all the small details and relevant OSS note references:
Top right in the details list there is the button to create the results document. This is easier for sharing the results with management, since they typically don’t have an S user to logon to the tool.
Running S4HANA ABAP checks in your own system
With the remote ATC tool with special variant S4HANA Readiness you can run the ABAP checks in your onw system. Read this blog for more information.
New content for new S4HANA versions
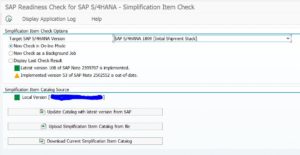
With every new version of S4HANA (and its intermediate feature packs) SAP will update the simplification list and the corresponding OSS notes. This will also impact the analysis programs. OSS note 2399707 – Simplification Item Check lists down which note version you need to apply to your system to have the checks for the S4HANA version of your choice. For the newer notes you will have to use the TCI based OSS notes (see blog on notes tips & tricks).
If you have installed the latest TCI note, you also get a new program called /SDF/RC_START_CHECK. After start of this program you get this screen:
You now can immediately see if you have new versions of OSS notes to apply to get most recent checks.
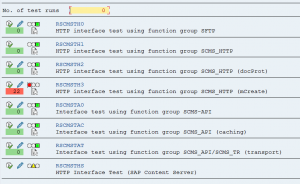
And after the run, you can use the button Application Log to see a more detailed result list on the simplification checks carried out in your system.
Custom ABAP code analysis
For a more detailed analysis on your custom ABAP code you can use the remote ATC tooling for a more detailed analysis. See this blog for details.