ABAP programs can be protected from changes by setting the editor lock. Only do this for very critical programs.
This blog will primarily focus on methods to remove the editor lock.
Editor lock
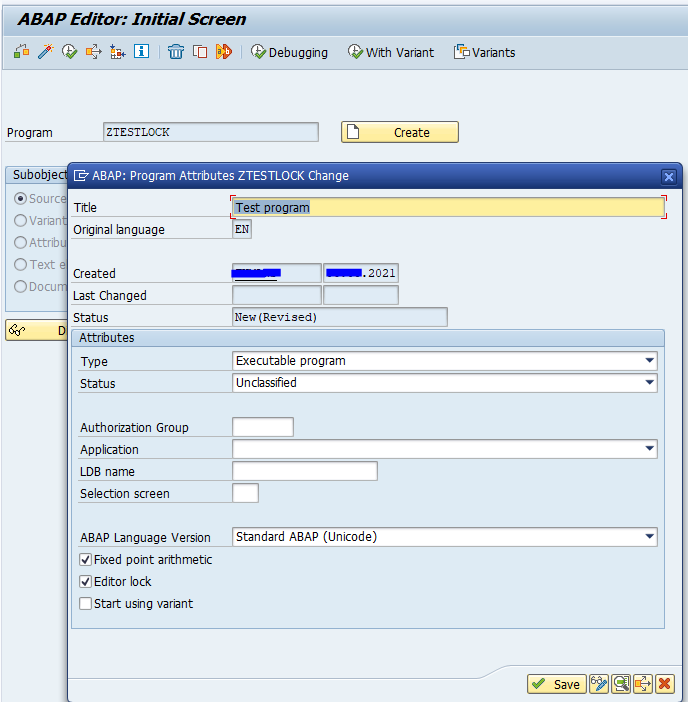
The editor lock is set on the properties of an ABAP program:
The property to set is the Editor Lock tickbox.
When this is set only the author can change the program.
Change user for editor lock
In some cases you have a valid reason to lift the editor lock. If the person has left, or you need to change the program for bug fixing emergency and you can’t wait until the owner is back.
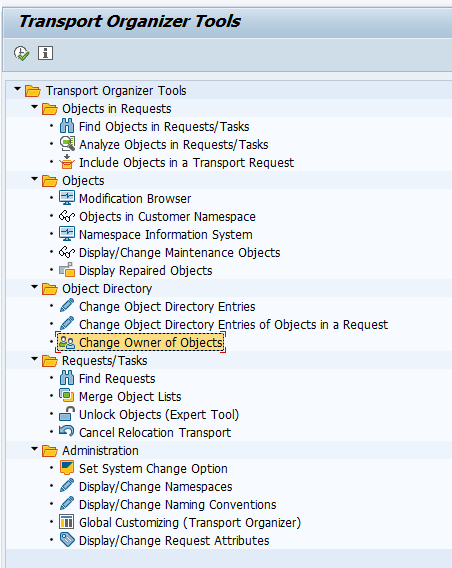
Change editor lock via SE03
As basis administrator you can change the owner of the editor lock in transaction SE03:
Change via SU01 usage
When person left: alter the password for this user in SU01. Log on as this user and remove the editor lock.
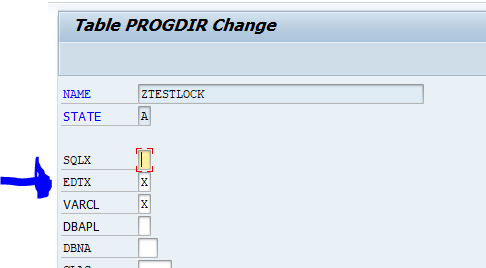
Via table editing of table PROGDIR
Goto table PROGDIR and view the content (via SE11). Search for your program and edit the entry:
Remove the EDTX flag and save. Editor lock is gone.
Via program
You can use Z program below to remove the lock:
REPORT zedit_lock_remove.
TABLES: trdir.
PARAMETERS: p_prog LIKE trdir-name OBLIGATORY.
START-OF-SELECTION.
SELECT SINGLE * FROM trdir WHERE name = p_prog.
IF sy-subrc = 0.
IF trdir-edtx = 'X'.
MOVE ' ' TO trdir-edtx.
MODIFY trdir.
WRITE: /'Editor Lock was removed from', p_prog.
ELSE.
WRITE: /'Program', p_prog, 'does not have an Editor Lock'.
ENDIF.
ELSE.
WRITE: /'No match found for program', p_prog.
ENDIF.